Before signing with a new MSP, it’s important to assess your current situation and gather key details about your existing environment. Many organizations discover during onboarding that their previous MSP didn’t fully document systems, share access information, or communicate clearly about what services were being provided.
Your MSP is strategic to your business operation and change is always uncomfortable, so it is usually avoided whenever possible. But resistance to changing MSPs can be a detriment to your business evolving. Taking that next step to become a market leader, attract new customers, hire a great employee, all are activities that benefit from complementing, strategic, technology systems.
If you are beginning to feel that your current MSP is inhibiting you from taking that necessary step to realize the full potential of your business, ask yourself these questions:
Do I receive regular reports and inventories? Your MSP should provide periodic inventory reports, network diagrams, and health summaries. If you’ve never received them, it’s worth requesting a full list of all managed systems before you transition.
Do I understand the current services and billing? Many businesses aren’t fully aware of what’s covered under their contract. Are you paying for cybersecurity monitoring, backups, and endpoint protection? Are there unexplained items on invoices? Clarify what you’re paying for now to avoid service gaps when you switch.
Has our MSP been transparent about access and information? A trustworthy MSP should provide you with administrative access, documentation, and system credentials. If they’ve held these closely, your new provider may face challenges gaining control of your environment.
Are we leasing or renting the IT hardware? Some MSPs lease hardware — such as firewalls, servers, or desktops — as part of their service. It’s critical to know which assets belong to you and which belong to your provider, since these may need to be replaced or returned during the transition.
Do we routinely review procedural checklists? Having shared documentation for tasks like onboarding new users, configuring endpoints, or provisioning accounts will make the changeover much smoother. If you don’t already have these checklists, your new MSP will likely create them as part of their onboarding process.
These questions not only prepare you for discussions to measure potential new provider(s), but they also help to identify potential risks or gaps that could delay onboarding when you decide it is time to make a switch.
Mileposts to Expect During a Change-Over
Switching MSPs is not a flip-of-a-switch event — it’s a structured process that typically unfolds over 30 to 60 days. During this period, both your old and new providers will need to coordinate to ensure business continuity. Here’s what you can expect throughout the transition:
- Kickoff and Recurring Meetings
The new MSP will host a kickoff meeting to introduce the project team, outline the timeline, and set milestones. Expect to see a detailed roadmap that defines who’s responsible for each step. - Hardware, Software, and Credential Inventory
Your new provider will inventory all servers, endpoints, network equipment, and applications. They’ll also review access credentials to confirm they have what’s needed to manage your systems. - Overlapping Support Period
A smooth transition usually includes about 30 days of overlapping support, where your old MSP continues handling tickets while the new one begins taking over. This overlap helps avoid service interruptions during the handoff. - Backup Verification
Before any major change, backups are tested and verified. This is critical — if something goes wrong during migration or toolset replacement, backups ensure data can be recovered quickly. - Transitional Introductions
Expect to participate in several “three-way calls” between your current and new providers to clarify responsibilities, hand off access, and confirm completion of specific tasks. - Transfer of Administrative Access
The new MSP will take over administrative accounts, while the outgoing provider’s access is restricted. Be aware that some outgoing MSPs may withhold certain credentials or procedural details. If this occurs, your new MSP will assist you in regaining control or rebuilding what’s missing. - Removal and Installation of Toolsets
Each MSP uses its own management tools for monitoring, remote access, and endpoint protection. During onboarding, your new provider will remove the old toolsets and install their own agents and utilities on your servers and devices. - License and Subscription Transfers
You may need to authorize the transfer of licenses or subscriptions, such as Microsoft 365, to your new MSP’s management. This includes updating the designated Cloud Solution Provider (CSP) or partner of record. - Training on Communication and Support Channels
MSPs have their own processes for submitting support requests — by phone, email, or client portal. Early in the relationship, your new provider should train your team on how to reach them and what information to include in requests. - Activation of SLAs
Once onboarding is complete, service level agreements (SLAs) go into effect. Response times and escalation paths should begin to normalize as the new MSP’s support systems take over.
- Post-Cutover Health Checks
After all systems are transitioned, your new MSP will perform health checks and audits to confirm that backups, security monitoring, and configurations are running correctly. These reviews ensure stability and compliance with your service plan.
Recommendations and Lessons Learned
As a leading Managed Service provider in central Pennsylvania, Morefield has successfully conducted many onboarding (and offboarding) projects for businesses across our service delivery area. We have worked with all types of businesses under our MSP program including Healthcare, Accounting, Legal, Consulting, Financial, Engineering, Manufacturing, Logistics and Transportation. Across this spectrum of experience, we have observed that organizations who approach MSP transitions thoughtfully tend to have the best outcomes. Here are some lessons we have learned from real-world onboarding projects:
Clarify expectations early. Before signing an agreement, review SLAs, escalation paths, and ticket workflows with your new MSP. Confirm how requests are prioritized and how after-hours support is handled to prevent frustration.
Request a complete IT asset inventory & documentation. Your current MSP should deliver a comprehensive list of all devices, servers, and network components under management. Technology documentation should also be shared such as up-to-date network diagrams, configuration backups, and environmental details. This becomes foundational for ongoing monitoring and lifecycle planning and accelerate troubleshooting.
Secure your passwords and access details. Request a copy of all system access credentials from your current MSP. If passwords are provider-specific, ask for them to be reset and shared securely with your organization and new MSP.
Plan for contingencies. Even with careful planning, tool migrations or firewall changes can cause unexpected downtime. Ask your new provider to review their rollback plans and contingency steps prior to scheduling the work.
Verify backups. Confirm all backup routines are operational and meet your retention | recovery goals. Backups are your last line of defense — never assume they’re running properly without verification. It is not unusual and better to expect that your current backup solution will be replaced by the new MSP, often this decision is contingent on how it was managed.
Confirm access revocation for the old provider. At the end of onboarding, ensure the new MSP has revoked all access previously granted to the outgoing provider — including VPN credentials, admin accounts, and shared passwords.
Following these lessons learned will help to protect your organization, it’s data and ensure a seamless handoff to your new managed service partner.
Inside Morefield’s MSP Onboarding Approach
At Morefield, we help central Pennsylvania businesses smoothly transition from one MSP to another. Whether we are welcoming them as a new customer to our Managed Program or supporting their decision to move on to their next MSP provider. The key elements of our structured onboarding plan are designed to minimize disruption, ensure accountability, and deliver transparency at every step.
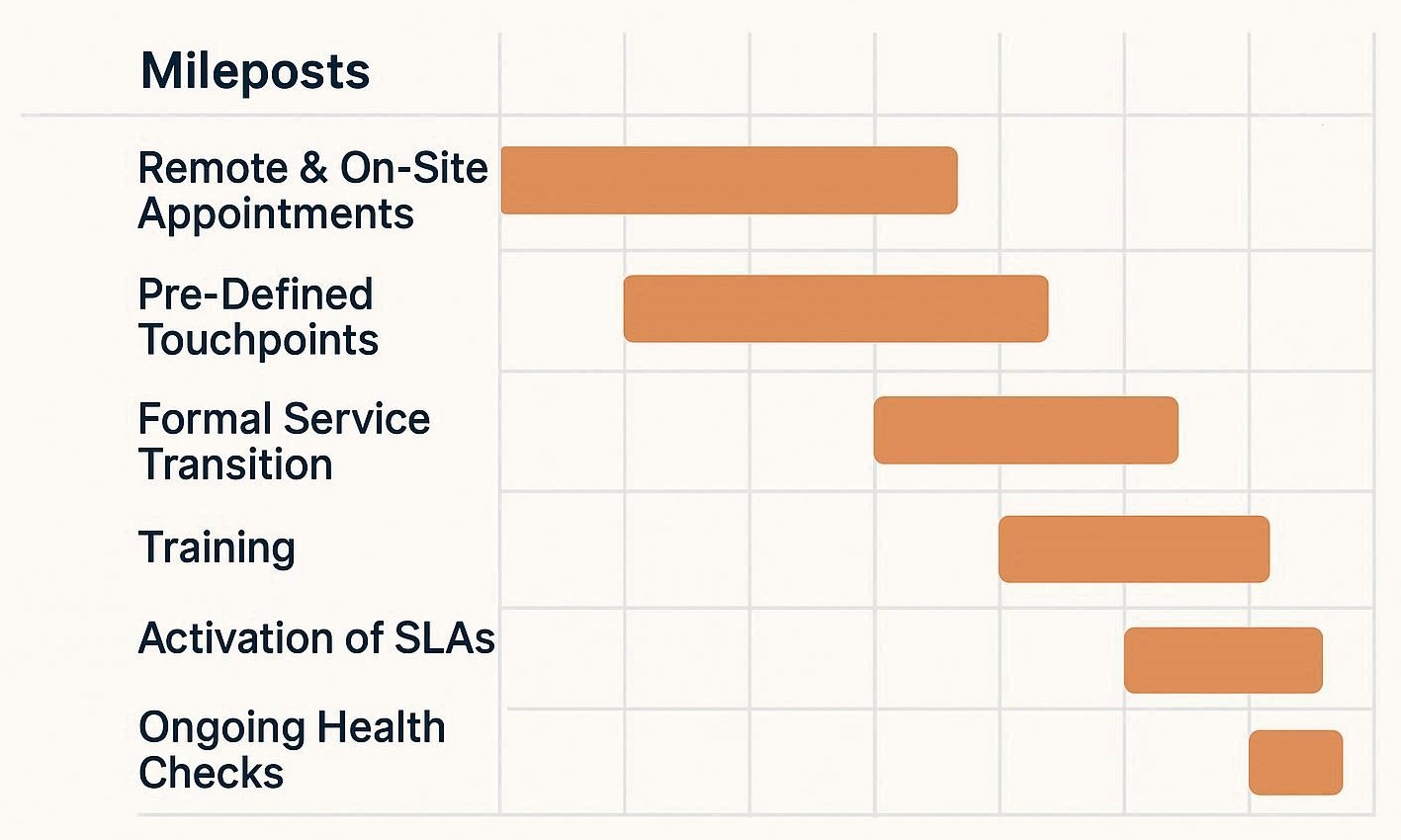
- Structured Project Plan
Every new client is assigned a dedicated project manager who serves as a single point of contact during onboarding. This ensures consistent communication and accountability. - Team-Based Execution
We take a collaborative approach, engaging experts in infrastructure, cybersecurity, and end-user support to cover every technical aspect of your environment. - Remote & On-Site Appointments
Our team performs a mix of remote and on-site activities to efficiently execute the onboarding plan and verify configurations firsthand. - Pre-Defined Touchpoints
You’ll experience clear milestones and check-ins throughout the project, so you always know what’s happening and when. - Formal Service Transition
Once onboarding is complete, there’s a structured handoff from the project team to our service delivery team, ensuring no detail is lost in the transition. - Training on Support Procedures
We provide training on how to submit requests via phone, email, or portal — so your employees can confidently engage our Service Desk from day one. - Activation of SLAs and Normalized Response Times
Once your systems are fully onboarded, our standard service levels go into effect, providing reliable response and resolution times. - Ongoing Health Checks and Audits
Morefield continues to monitor your systems through scheduled appointments, health checks and audits to verify performance, stability, and compliance with your program.
Make a Confident Start With Your New MSP
Changing MSPs can feel daunting, but with the right plan, it’s an opportunity to gain greater visibility, better support, and stronger alignment with your business goals. By understanding what to expect — from early planning through final cut-over — you can set realistic expectations, avoid disruptions, and ensure your technology foundation is in capable hands.
A successful transition isn’t just about new tools or contracts; it’s about establishing a relationship built on trust, transparency, and proactive service. With a structured approach like Morefield’s, you can make the change with confidence and look forward to a more strategic, responsive IT experience. When you are ready to learn more about the many benefits of Morefield’s Managed Service Program, contact us.