How Can Companies Prevent Security Breaches?

Data is the lifeblood of modern organizations. Secure data is essential for protecting sensitive information, maintaining customer trust, complying with regulations and ensuring business continuity. Data breaches rose to a record high in 2023 with over 3,200 reported breaches — that’s a 78% increase from 2022. A data breach, also known as data leakage, is any form of unauthorized access, exposure, disclosure or loss of confidential information.
Compromised data can result from a variety of motives from external attackers aimed at gaining unauthorized access to financial records, credit card numbers, social security number or bank account information. Vigilance against unending, evolving threats can cause data breach fatigue — leading to complacency with cybersecurity and lax in employee awareness. It’s essential for your company to learn how to prevent data leakage to maintain its security posture and stay a step ahead of hackers.
How Do Data Breaches Happen?
Though many people assume security breaches are always a result of intentional attacks, they can also be caused by unintentional flaws in your company’s infrastructure or employee oversight. Below, we’ve outlined other common ways a security breach can occur:
- Human error: Employees can accidentally cause a data breach by making simple mistakes, such as emailing confidential information to the wrong recipient when distracted, having easy-to-guess passwords or failing to update their software to patch vulnerabilities.
- Malicious insiders: Data breaches can occur by an insider deliberately misusing their access to your company systems as an act of revenge or sabotage. They can use their authorized access to get the company’s trade secrets, financial details, passwords, client lists and other sensitive information to harm the organization or an individual. Some may even sell this information to competitors or hackers in exchange for profit.
- Lost or stolen devices: Confidential data can easily be breached when documents, laptops, phones or hard drives are lost or stolen. Employees leaving sensitive documents unattended is an easy opportunity for individuals with malicious intent. Anything that contains sensitive information can pose a major risk if it ends up in the wrong hands, especially if it’s unlocked and unencrypted.
- Targeted attack: Outside criminals will use various techniques to obtain confidential information from a network or individual. These methods include social engineering tactics that manipulate users into divulging sensitive data, tricking users into opening malicious software attachments and crashing a company’s network by flooding it with fake requests.
The Widespread Impact of Security Breaches
Companies of all sizes and types are vulnerable to a data breach. The average cost of a data breach in 2023 was $4.45 million, increasing by over 15% since 2020. While these immediate financial losses can be devastating, data breaches have a far-reaching impact that can affect your entire organization in many other direct and indirect ways.
The ramifications of a security breach can result in:
- Reputation damage
- Increased operational costs
- Financial penalties
- Operational downtime
- Difficulties in achieving company growth
- Legal claims and expenses
- Reduced customer loyalty
- Poor public reception of your company
- Public relations expenses
- Erosion of trust with existing and new consumers
- Challenges in generating revenue in the future
- Compromised company sustainability
Best Practices for Preventing Data Breaches
Even the smallest vulnerability can put your entire organization at risk for a security breach. If you want to learn how to prevent a data breach in your company, follow these tips to reduce organizational exposure.
1. Educate and Train Employees
A study revealed that 88% of data breaches were caused by employee mistakes. Employees are often your first line of defense, which is why cybersecurity awareness training should be a mandatory component of employee onboarding and continued learning.
Be sure to teach employees about the most common threats to your specific organization and how to avoid them. Are your employees at risk for social engineering ploys, fraudulent emails or being tricked into handing over sensitive details? Provide regular training that encourages them to stick to the best cybersecurity practices, including:
- Using strong passwords
- Changing passwords often
- Using a different password for every account
- Staying up-to-date with the latest threats
- Using multi-factor authentication (MFA) to prove their identity
- Implementing access controls to protect data and resources
- Updating software when prompted to do so
- Avoiding phishing and other social engineering scams
2. Develop an Incident Response Plan
Do your employees understand their role in the event of a data leak or breach? Creating a well-designed incident response plan (IRP) equips your team with clear steps to quickly respond to a data threat or data breach. Your IRP should include ways your employees and security teams can detect, contain and eradicate cyberthreats as soon as possible.
Your teams should also know who is responsible for reporting a data breach, discover what data was compromised and monitor your network for other malicious activity. You may even create a dedicated response team to mitigate the damage and costs of these events.
3. Perform Regular Security Audits
Regulatory and internal compliance are an obligation in most industries, including government and finance. If your company has a poor data security strategy, you can risk overlooking vulnerabilities and threats until it’s too late. Scheduled internal audits can prevent data breaches by ensuring your organization maintains compliance with ever-changing regulations and cyberthreats.
Performing audits offers an opportunity to eradicate old practices, gaps in security and weak controls in your existing systems and networks. You can also identify if your employees have drifted from your polices, protocols and procedures by auditing your processes regularly.
4. Maximize Your Company’s Cybersecurity Practices
A strong internal security strategy is key to protecting your company against vulnerabilities that could lead to a breach. However, detecting and preventing security threats is a collaborative effort. For small- and medium-sized businesses, there may not be ample resources to create a dedicated security team to stay on top of minimizing compromise risk.
You can implement proactive, comprehensive cybersecurity services by working with a trusted technology solutions provider. Business cybersecurity services will help you make the necessary improvements to minimize risk so you can focus on other organizational objectives.
Why Trust Morefield for Data Breach Protection?
With so many new data threats evolving, it can be more and more challenging to enhance your organization’s security. Outdated and weak security measures can lead to significant data and financial losses at your company.
At Morefield, we want to help you protect your core systems, processes and networks that breathe life into your organization. We recognize that preventing and responding to cyber threats requires continuous work, which is why we offer a range of resource and management tactics to keep your business safe.
With our innovative, integrated solutions that address your specific problems and grow with your company’s needs. Our technicians and engineers maintain the highest level of qualifications and professionalism to properly care for every facet of your business technology. You can rely on fast response times, remote software upgrades and greater efficiency across your entire company.
Stay Ahead of Cybersecurity With Morefield
Protecting your company’s data against never-ending security threats can be challenging to sustain. When you work with Morefield, we’ll help you meet your company’s cybersecurity needs by identifying potential weaknesses and risks. It’s our goal to help organizations make smarter technology decisions and enhance compliance. Our scalable cybersecurity solutions protect your sensitive data and reduce the consequences of an unexpected data breach.
With our wide variety of services, you can defend the availability, integrity and confidentiality of your data. We encourage you to schedule a cybersecurity assessment with us today to learn more about preventing security breaches.
Business Happy Hour with Langan Financial & UPMC Child Life Program
We teamed up with Langan Financial to host a Spring happy hour, on at their office at 1863 Center Street, Camp Hill.
We had delicious food from Dodge City once again as well as fresh flower bouquets for our guests.
We were happy to support UPMC’s Child Life Program at UPMC Children’s Harrisburg. A program that plays a crucial role in supporting children and families during medical challenges or hospitalization. This program provides pivotal care for children through education, training, and what I consider a vital aspect – helping a child maintain their childhood as much as possible during hospital stays.
If you were unable to attend, but would still like to support them here is a link to their wish list : Amazon.com
Manufacturers’ Association Spring Networking Event

We had a wonderful night networking with the Manufacturers’ Association and others in the industry. Thank you to everyone that came out and kicked off the spring weather at this great venue in York.
| Date and Time: Wednesday, April 24th 4:30-6:30pm EDT | Location: South County Brewing Company, The Virgil Room, 170 Crossway Drive, York, PA 17402 |


How to Minimize Network Downtime and Increase Efficiency

With so many business activities occurring online, downtime can be disastrous for modern organizations — and its frequency and financial effects are only increasing. In the Uptime Institute’s 2022 report, over 60% of outages cost at least $100,000 in total losses, and almost a third lasted over 24 hours. Both values reflect substantial increases from prior years.
Unfortunately, many sources can cause downtime. Pinpointing the issue may not be straightforward, leading to time-consuming fixes. We’ve outlined some strategies for reducing unplanned downtime to help you keep your business moving and limit the effects of outages.
Downtime Reduction Strategies
Prevention is the best way to limit downtime. Whether you currently face issues with downtime or want to stay prepared, try these tactics to avoid problems.
1. Audit and Monitor Your Entire System
Start by thoroughly analyzing your entire system, including internal and external risks. During this process, you’ll identify weak points that can tell you where to focus your efforts. Look for potential issues by reviewing every asset, including:
- Routers
- Servers and software
- Power supplies
- Cables
- Cloud service providers
- Internet service providers
- Utility providers
Document any possible vulnerabilities. If a network outage occurs, you can check these vulnerabilities first to minimize the length of downtime. With the complete picture of your IT infrastructure, you can implement constant monitoring for each network component. Real-time monitoring solutions allow you to respond faster, preventing downtime and minimizing the workload.
2. Build Redundancy
With a redundant network connection, you can seamlessly switch from one ISP to another if your primary provider goes down. Redundant systems help reduce the damaging effects of errors or shutdowns and ensure continued operations. If you have speed issues, a redundant network might also offer more paths for accessing data, allowing you to use the fastest one at a given time.
Data redundancy is valuable, too. Storing your information in a secondary location with backup services can ensure access to critical resources even if your primary data storage site goes offline.
3. Implement Backup Power
Another type of redundancy is backup power. An uninterruptible power supply detects when the primary power source fails, powering up immediately to keep your electronics online. These devices typically provide power for about 30 to 60 minutes — plenty of time to save work and safely shut down electronics. This time frame is also enough to support tasks like making sales or accessing information during brief periods of power interruption.
A UPS handles power conversions for highly sensitive technology, so you should include it in your maintenance and testing plans.
4. Create a Robust Maintenance Strategy
Maintenance is crucial for any IT infrastructure. From routine firmware and software updates to equipment configurations and testing, robust maintenance supports your devices’ ongoing performance. Ensure your plan includes preventive maintenance, which involves identifying and fixing problems before they cause unplanned downtime.
5. Invest in Quality Equipment
Always select your IT equipment for the job at hand and invest in high-quality systems. While quality hardware might cost more upfront, reliable performance and reduced downtime can save you significantly in the future.
Solutions to Common Networking Problems
The Uptime Institute report found networking issues to be the top cause of IT service downtime incidents. Even if it doesn’t cause a complete outage, a slow network can adversely impact your efficiency, limiting your ability to conduct day-to-day operations. If you frequently experience lagging apps, slow Internet speed, interrupted voice calls and other connection problems, assessing your network could help you improve operational efficiency.
Network downtime can happen due to these internal and external factors.
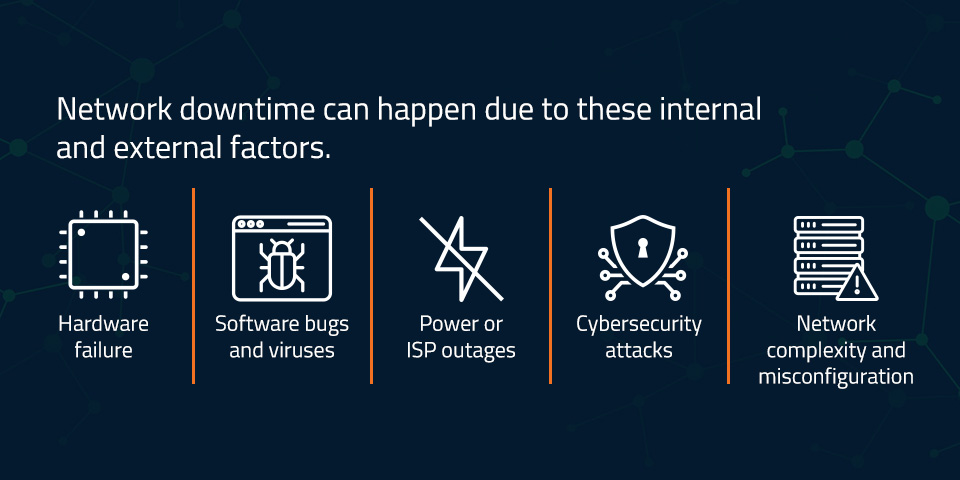
- Hardware failure: Many types of hardware can fail due to age, damage and overheating. Even something as innocuous as a cable chewed up by a mouse can lead to costly network outages. Some networking devices that deserve special attention include firewalls, routers, switches and network interface cards. Regularly evaluate your hardware assets’ condition and capabilities.
- Software bugs and viruses: Software issues can cause network problems, too. Perform firmware and software updates as needed, and regularly evaluate your software solutions to keep these issues at bay.
- Power or ISP outages: Utility providers and ISPs often have outages due to inclement weather conditions like high winds or blizzards. Other reasons you might have an outage include wildfires and damage to infrastructure, like a downed power line from a fallen tree. Redundant networks and power backups can mitigate these unpredictable circumstances.
- Cybersecurity attacks: Cybersecurity attacks like denial of service and spoofing can target your network. You can better resist cybersecurity threats by following comprehensive security practices, including network monitoring.
- Network complexity and misconfiguration: Highly complex networks often create opportunities for human error and misconfiguration. You can minimize risk with straightforward IT infrastructure, transparent workflows and a knowledgeable team.
Continuous monitoring is one of the best ways to prevent network downtime and boost efficiency. Once in place, it can help you determine which devices cause problems under what scenarios. Effective monitoring software can reduce your team’s workload and minimize human error. Since networking issues have many potential sources, monitoring allows you to respond flexibly to different scenarios.
Apply thorough network monitoring at strategic points throughout your network, such as routers, switches and user devices. Developing a remote monitoring solution can help you build an at-a-glance view of how data flows across the network. It delivers real-time information for quickly pinpointing problem areas and preventing or shortening outages. Monitoring can also offer insights into long-term needs, such as future upgrades or changes in capacity.
As you monitor the network, collect data on its behavior to establish baselines. For example, you might gather information on bandwidth and latency during typical usage conditions. Once you know how your network usually behaves, you can determine thresholds and set up alerts for out-of-range situations. Investigating alerts also becomes simpler, as you can quickly analyze traffic routes to optimize performance.
Maximize Uptime With Morefield
When power or networking issues affect a business, they can bring operations to a halt and significantly increase costs. They can even put your reputation or compliance at risk. Tackling downtime calls for a comprehensive approach and knowledgeable IT professionals. If you do business in Pennsylvania, work with the experts at Morefield.
We offer a wide range of services, including managed IT services that allow our experienced team to handle time-consuming tasks like maintenance, backups and tech support. We can also offer support in specific areas like cybersecurity and wireless networking. Reach out today to discuss how we can optimize your uptime.

