If you’re evaluating access control for your facility in Central Pennsylvania, you’re probably asking a straightforward question:
“What is this actually going to cost us?”
And if you’ve already started researching online, you’ve likely found answers that feel vague, overly generic, or disconnected from reality.
The truth is this: access control pricing does depend — but not in a mysterious way. Once you understand what drives cost, you can build a realistic budget and avoid the surprises that frustrate so many organizations.
This guide is written for organizations located in the counties and communities of Central Pennsylvania — from Lancaster and York to Dauphin, Cumberland, Berks, Lebanon, Adams, and surrounding areas.
Let’s break it down clearly.
First, What Are You Actually Paying For?
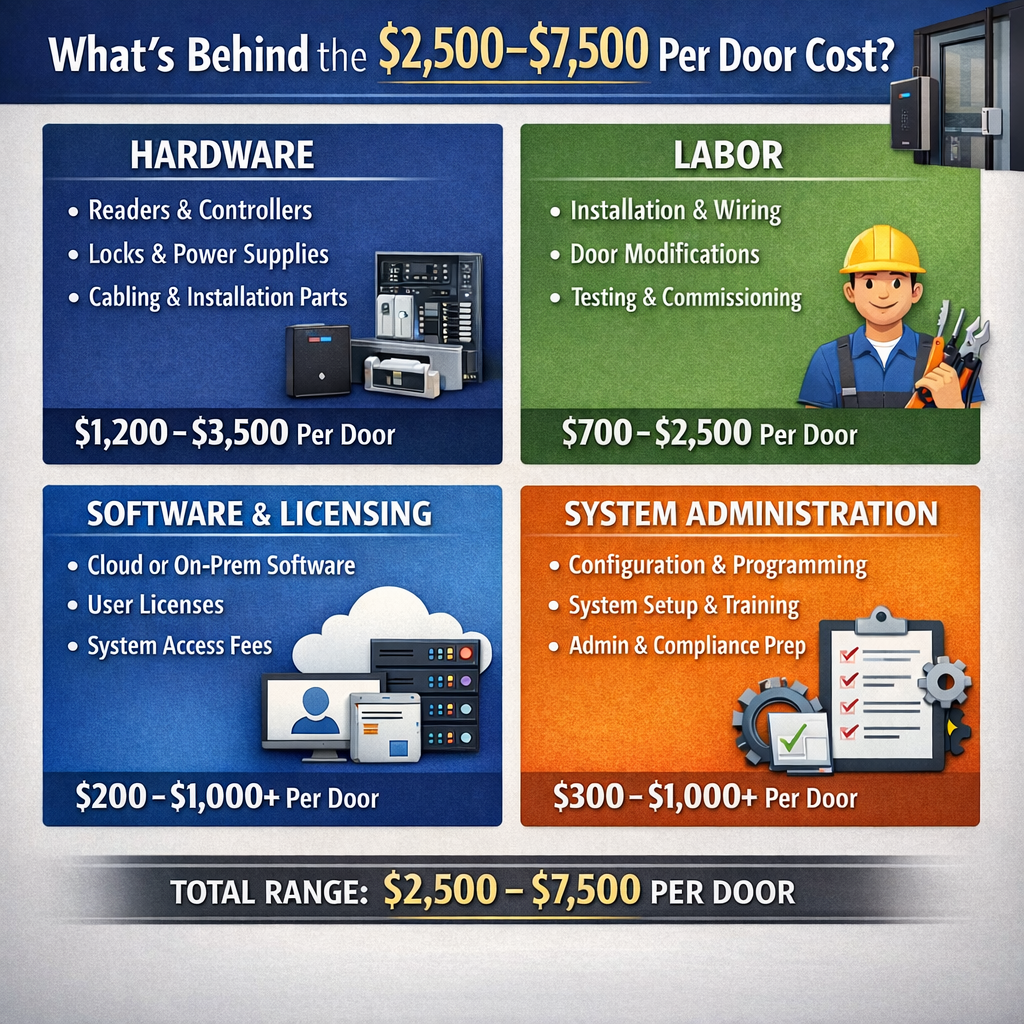
A modern access control system has three cost layers:
- The physical door hardware and installation
- The software platform that manages permissions and reporting
- Ongoing administration, maintenance, and support
Most budget confusion happens when companies only think about the hardware. But access control today is not just a lock upgrade. It’s a connected security platform that affects compliance, operations, and risk management.
For commercial environments a realistic planning range in Central Pennsylvania for a professionally installed, modern access control system typically falls in the range of $2,500 to $7,500 per controlled door in year one
That range reflects where Morefield expertise is contracted across:
- Professional office buildings
- Medical and outpatient facilities
- Light industrial and warehouse spaces
- Multi-site service organizations
- Education and nonprofit environments
Some doors will fall below this range. But this gives a practical budgeting framework grounded in our region’s labor market and building conditions. Now let’s unpack why.
The Biggest Cost Variable: The Door Itself
In Central Pennsylvania, our region is rich in history and heritage. But that also means that we work with a wide range of building types:
- Older brick construction in Lancaster, York, and Harrisburg
- Retrofitted manufacturing spaces in Lebanon and Berks counties
- Modern office developments in Cumberland County
- Converted industrial and mixed-use facilities across the territory
Each type presents different challenges. An interior solid-core office door with accessible ceiling space for wiring is relatively straightforward. But the many types of exterior doors across the region add complexity as:
- Aluminum storefront frames
- Glass entryways
- Masonry walls that require core drilling
- Limited existing power near the door
- Fire-rated doors requiring code-compliant electrified hardware
That complexity affects both material and labor costs. Two doors may look similar from the outside, but one might require 6 hours of labor — and the other a lot of creativity, investment that can equate to 1-2 days on a job site solely focused on an installation for one door.
Regional Labor Considerations
Commercial low-voltage labor rates in Central Pennsylvania range between $100–$150 per hour, depending on the contractor and project scope. This is generally lower than major metro markets like Philadelphia or New York but still reflects skilled labor rates. A typical door installation requires:
- Hardware mounting
- Wiring and cable management
- Power supply installation
- Controller setup
- Software configuration
- Testing and commissioning
When labor is combined with hardware and configuration time, it significantly contributes to the total per-door investment.
Hardware and Technology Choices
Hardware pricing does not vary dramatically by geography, but the choices that you make for your access control system will influence the final cost. For example, a standard card/fob system will tend to have lower upfront credential costs. Whereas mobile credential systems usually involve subscription per-user licensing.
Higher-security environments require more expensive reader hardware paired with encrypted credentials for critical doors. Building’s exterior doors require robust locking hardware and fail-safe mechanisms for egress that are usually absent from interior doors.
Most professionally deployed commercial systems use enterprise-grade components — not consumer or DIY hardware — because they must withstand daily traffic and security demands. That reliability matters.
For controlling the door hardware, cards, fobs and mobile credentials, modern access control platforms are typically either Cloud-managed or managed through an on-premises server.
In Central Pennsylvania, we increasingly see organizations choosing cloud-managed systems because they:
- Reduce on-site server requirements
- Simplify remote management
- Allow multi-site visibility
- Push security updates automatically
While cloud systems introduce ongoing licensing, they often reduce long-term infrastructure headaches and IT overhead. The perpetual licenses vary amongst manufacturers but most base the licensing costs on the number of doors, number of users and then any advanced feature sets or integration needs
Hidden Costs That Affect Budgeting
Here’s where many Central PA organizations underestimate total cost.
Networking and Cybersecurity
Access control is connected technology. It touches your network, relies on connectivity to operate. That means the network should be segmented with VLANs to isolate the controller traffic. Firewall rules will need to be in placed to allow for access to Cloud control portals as well as secure remote access.
If your organization must meet compliance standards (healthcare, financial services), this layer becomes even more important.
Project Management and System Administration
Professional implementation includes:
- Door behavior testing
- Fail-safe vs fail-secure validation
- Fire code compliance checks
- Access group configuration
- Credential lifecycle setup
- Admin training
When these steps are skipped or rushed, systems become unstable. That instability costs far more in the long run and ongoing operation of the system.
What Impacts Cost in Central Pennsylvania?
where regional context really matters.
- Older Building Retrofits
Many facilities in our region were not originally built with low-voltage infrastructure in mind. Retrofitting wiring through masonry walls, plaster lathe, or inaccessible ceilings increases labor.
- Multi-Site Growth
It’s common for Central PA businesses to expand across neighboring counties — opening satellite offices or warehouses. That growth influences whether you design a scalable platform from the start.
- Weather and Exterior Durability
Our climate — snow, humidity, freeze-thaw cycles — requires exterior hardware rated for those conditions. Cutting corners on exterior components leads to unpredictable operation of the system or early failure of components.
- Skilled Labor Availability
Central PA has strong skilled trades, but availability can fluctuate. Scheduling and project timelines should factor into planning — especially for larger deployments.
Building a Realistic Budget
If you’re early in planning, start with three questions:
- How many doors need control today?
- How many might need control within 2–3 years?
- Are we solving only a security issue — or also operational inefficiencies?
Then use the $2,500–$7,500 per door regional planning range as your baseline, understanding that complexity pushes you higher and simplicity brings you lower. For multi-door projects, economies of scale can reduce per-door averages because controllers and infrastructure are shared across the facility.
Access Control for Central PA Organizations
Access control in 2026 is not just about locking doors. It’s about:
- Protecting people
- Reducing operational friction
- Supporting compliance
- Enabling controlled growth
- Integrating physical and digital security
For most organizations in Central Pennsylvania, a well-designed, professionally implemented system will represent a meaningful but manageable investment.
The key isn’t finding the lowest number. It’s building a system that works reliably, scales with your organization, and strengthens your overall security posture.
When you want to understand the cost drivers, to plan your next system confidently — contact Morefield and avoid the frustration that comes from underestimating what it takes to do it right.