On-Demand Webinar – Cybersecurity 101: Practical Strategies for Every Business
| Cybersecurity 101: Practical Strategies for Every Business presented by Michael Velasco of Morefield Originally held Tuesday, March 12th, 9:30-10:30 a.m. on Zoom |
| Cybersecurity 101: Practical Strategies for Every Business presented by Michael Velasco of Morefield Originally held Tuesday, March 12th, 9:30-10:30 a.m. on Zoom |

Browser extensions have become as common as mobile apps. People tend to download many and use few. There are over 176,000 browser extensions available on Google Chrome alone. These extensions offer users extra functionalities and customization options.
While browser extensions enhance the browsing experience, they also pose a danger which can mean significant risks to online security and privacy.
In this article, we unravel the dangers associated with browser extensions. We’ll shed light on the potential threats they pose as well as provide insights into safeguarding your online presence.
Browser extensions are often hailed for their convenience and versatility. They are modules that users can add to their web browsers. They extend functionality and add customizable elements.
From ad blockers and password managers to productivity tools, the variety is vast. But the ease with which users can install these extensions is a weakness because it also introduces inherent security risks.
Next, we’ll delve into the hazards associated with browser extensions. It is imperative to strike a balance between the benefits and dangers.
Many browser extensions request broad permissions. If abused, they can compromise user privacy. Some of these include accessing browsing history and monitoring keystrokes. Certain extensions may overstep their intended functionality. This can lead to the unauthorized collection of sensitive information.
Users often grant permissions without thoroughly reviewing them. This causes them to unintentionally expose personal data to potential misuse.
There are many extensions developed with genuine intentions. But some extensions harbor malicious code. This code can exploit users for financial gain or other malicious purposes. These rogue extensions may inject unwanted ads. As well as track user activities or even deliver malware.
These extensions often use deceptive practices. They make it challenging for users to distinguish between legitimate and malicious software.
Extensions that are no longer maintained or updated pose a significant security risk. Outdated extensions may have unresolved vulnerabilities. Hackers can exploit them to gain access to a user’s browser as well as potentially compromising their entire system. Without regular updates and security patches, these extensions become a liability.
Some malicious extensions engage in phishing attacks as well as social engineering tactics. These attacks can trick users into divulging sensitive information.
This can include creating fake login pages or mimicking popular websites. These tactics lead unsuspecting users to unknowingly provide data. Sensitive data, like usernames, passwords, or other confidential details.
Certain extensions can significantly impact browser performance. This can happen due to being poorly coded or laden with unnecessary features. This results in a subpar user experience. It can also lead to system slowdowns, crashes, or freezing. An extension’s perceived benefits may attract users but they end up unwittingly sacrificing performance.
Download extensions only from official browser marketplaces such as those connected with the browser developer (Google, Microsoft, etc.). These platforms have stringent security measures in place. This reduces the likelihood of encountering malicious software.
Before installing any extension, carefully review the permissions it requests. Be cautious if an extension seeks access to unusual data such as data that seems unrelated to its core functionality. Limit permissions to only what is essential for the extension’s intended purpose.
Regularly update your browser extensions. This ensures you have the latest security patches. Developers release updates to address vulnerabilities and enhance security. If an extension is no longer receiving updates, consider finding an alternative.
It’s tempting to install several extensions for various functionalities. But each added extension increases the potential attack surface. Only install extensions that are genuinely needed. Regularly review and uninstall those that are no longer in use.
Use reputable antivirus and anti-malware software. This adds an extra layer of protection against malicious extensions. These tools can detect and remove threats that may bypass browser security.
Stay informed about the potential risks associated with browser extensions. Understand the permissions you grant. Be aware of the types of threats that can arise from malicious software. Education is a powerful tool in mitigating security risks.
If you encounter a suspicious extension, report it. You should report it to the official browser extension marketplace and your IT team. This proactive step helps browser developers take prompt action. That action protects users from potential threats.
Conduct regular audits of the extensions installed on your browser. Remove any that are unnecessary or pose potential security risks. Maintain a lean and secure browsing environment. This is a key aspect of online security.
Browser extensions are just one way you or your employees can put a network at risk. Online security is multi-layered. It includes protections from phishing, endpoint threats, and more.
Don’t stay in the dark about your defenses. We can assess your cybersecurity measures and provide proactive steps for better protection.
Give us a call today to schedule a chat.
This Article has been Republished with Permission from The Technology Press.

In the digital age, data is the lifeblood of businesses. It fuels operations, decision-making, and customer interactions. But there is a dark underbelly of this data-centric landscape. It’s the persistent threat of data breaches.
The repercussions of a data breach extend far beyond the immediate aftermath. They often haunt businesses for years. Only 51% of data breach costs occur within the first year of an incident. The other 49% happen in year two and beyond.
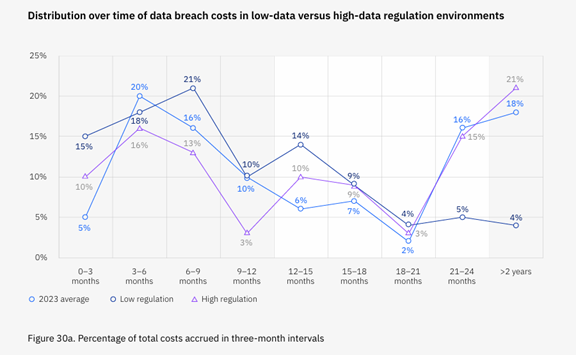
We’ll take a look at the long-term consequences of a data breach. As well as examine a real-world example. You’ll see how a single breach can have enduring implications. Ones that impact a business’s reputation, finances, and regulatory standing.
Introduction to the First American Title Insurance Co. Case
The 2019 cybersecurity breach at First American serves as a stark illustration. It reminds us of the far-reaching consequences of a data breach. In this case, the New York Department of Financial Services (NYDFS) imposed a $1 million fine. Cybersecurity sites announced the fine in the fall of 2023. The company’s fine was for failing to safeguard sensitive consumer information.
The breach exposed over 880 million documents. These files contained personal and financial data. The breach represented a significant violation of data protection standards.
This is one example of how costs can come long after an initial breach. Here are some other ways security incidents can haunt businesses for years.
The financial toll of a data breach is significant. Immediate costs include things like:
Beyond those, businesses face long-term expenses. These relate to legal battles, regulatory fines, and reparations. Regulatory penalties are just one facet of the financial repercussions. Others include potential legal actions from affected individuals. As well as class-action lawsuits adding to the monetary strain.
The impact on a business’s reputation is arguably the most enduring consequence. Customers lose trust in a company’s ability to protect their sensitive information. This loss of trust can result in a decline in customer retention. As well as acquisition difficulties and long-lasting damage to the brand image.
Rebuilding a tarnished reputation takes time. It also takes concerted efforts. These may involve public relations campaigns and enhanced security measures. These actions help assure stakeholders of renewed commitment to data protection.
Regulatory bodies increasingly hold businesses accountable for safeguarding consumer data. A data breach triggers regulatory scrutiny. This may lead to fines and ongoing compliance requirements.
Regulatory authorities take a stringent stance on data security. As well as on companies that fail to meet cybersecurity standards. The fallout includes financial penalties. As well as increased oversight and mandatory security improvements.
The aftermath of a data breach disrupts normal business operations. Companies must take remediation efforts and put in place enhanced security measures. These can divert resources away from core business functions.
The company feels the impact across departments, affecting productivity and efficiency. The ripple effect of operational disruption can extend for years. This impedes growth and hinders the organization’s ability to adapt to market changes.
A data breach often leads to customer churn. Individuals lose confidence in the business’s ability to protect their data. Acquiring new customers becomes challenging. Potential clients are wary of associating with a brand that has suffered a breach. The prolonged effects on customer acquisition can hinder the company’s growth. As well as its market competitiveness.
The repercussions of a data breach extend far beyond the immediate incident. They can impact the financial health and reputation of a business for years. As well as its regulatory standing.
The frequency and sophistication of cyber threats continue to rise. Proactive cybersecurity measures are not just a necessity. They are a strategic imperative for safeguarding the long-term success of businesses.
The true cost of a data breach is not always immediately evident. It’s a complex interplay of things like:
These impacts can persist for years. It’s important to learn from real-world examples. As well as focusing on robust cybersecurity measures. This helps businesses mitigate the risks associated with data breaches. As well as safeguarding their immediate interests and their long-term viability.
There are many ways that hackers can breach a network. From endpoints to cloud tools, you must run a tight security ship. Need some help? Morefield can help.
Schedule a cybersecurity assessment with us today. This is the first positive step into understanding and addressing your risk. As well as avoiding the consequences of a data breach.
Give us a call today and schedule an assessment.

Insider cybersecurity threats can wreak havoc on your business or organization’s critical operations. Understanding how and why they happen is key to finding solutions to keep bad actors from accessing your private information and systems.
Here, we are sharing everything you need to know about these types of threats and how the right security measures can help your organization successfully mitigate insider risks.
With cybercrime reaching an all-time high in 2023, businesses must enhance their methods for protecting their sensitive information and systems. The consequences of an attack or data breach can be detrimental to your operations, so learning more about the different types of threats can help you mitigate risks in your digital environment before they become major issues. An element of cybersecurity that enterprises often overlook is insider threats.
An insider threat refers to a cybersecurity risk posed by an individual to whom your business or organization granted authorized access to your private resources, networks or devices. Insiders may include employees, partners, contractors or anyone you trust with knowledge about and credentials for your systems. There are two main types of insider threats — intentional and unintentional.
Intentional threats involve an insider deliberately misusing their access to your organization’s systems. They may be interested in interrupting your operations or stealing information for personal gain. Potential motives behind insider threats include:
Unintentional insider threats occur when a well-meaning individual inadvertently compromises access to your business’s systems or network. Through negligence, lack of awareness or errors, that person accidentally created a vulnerability that cybercriminals can capitalize on to harm your operations.
Common unintentional insider cybersecurity threats include the following:

According to the United States Cybersecurity and Infrastructure Security Agency, the fundamental framework for mitigating insider threats includes these steps:
The following are a few helpful tips for combating insider threats with this essential framework in mind:
An effective way to avoid unintentional insider risks is to provide your personnel with comprehensive training on cybersecurity best practices. When your team is aware of the potential risks, they can make more informed decisions when they believe they’ve witnessed something suspicious. Proper education and training are key to fostering a secure and aware culture at your company. Teach your team what scams and threats may look like and encourage them to report any concerning behavior or activity to management.
Another beneficial tip for combating insider threats is to perform regular cybersecurity assessments. Cybersecurity experts can evaluate your entire digital environment and look for gaps in your protections that cybercriminals could potentially capitalize on.
Periodically assessing your processes and online landscape can help you proactively address weaknesses and implement new strategies to minimize vulnerabilities.
Your access controls can make or break your organization’s cybersecurity posture. Regularly review and update your access permissions and credentials to ensure that only specified personnel can reach your critical systems. It can be helpful to restrict user privileges to include only the necessary information or resources needed to fulfill their specific responsibilities.
Businesses and organizations can minimize the negative impacts of an insider cybersecurity threat by establishing a comprehensive incident response plan outlining the protocols your team will take if an incident occurs. These plans should include the following:
Data loss prevention (DLP) solutions help organizations monitor user activity and detect attempted breaches to better protect your sensitive information. They can reinforce your data policies and minimize the chance of unauthorized access to your systems. You can improve security for your users, customers and proprietary information with the right tools.
With a 40% increase in insider risk incidents from 2019 to 2023, businesses and organizations must find effective methods for protecting their sensitive information and systems. Explore the following reasons why identifying potential insider threats is critical for your operations:
At Morefield, we understand how crucial it is to have a comprehensive cybersecurity solution for your business. Our services are here to help your organization secure its digital operations and protect your private data.
We can help with a variety of cybersecurity-related solutions, including vulnerability assessments, mobile device management and more. Your business can also turn to us for virtual chief information security officer services to gain access to affordable cybersecurity expertise and assistance.
Are you ready to learn more about protecting your business? Explore the cybersecurity solutions from Morefield and connect with us online to get started today.


Cyber hygiene can be the difference between a detrimental data breach and business as usual for your company. At Morefield, we have decades of experience in the cybersecurity sector, and we understand the changing landscape for businesses like yours. Explore the practices you can follow to secure your operation’s digital environments and protect your private information from cybercriminals.
Cyber hygiene, sometimes called cybersecurity hygiene, refers to the set of principles and protocols an organization or person uses to secure their digital landscape, including:
These practices are often part of a larger ongoing routine dedicated to maintaining a healthy system and keeping private information safe from unauthorized personnel and cyberattacks.
With a whopping 83% of organizations enduring more than one data breach in 2022, businesses must take the growing threat of a cyberattack very seriously. Without proper cyber hygiene practices, your operation risks jeopardizing sensitive information about your customers, employees, proprietary solutions, intellectual property and company financials.
One data breach can be enough to compromise your business’s reputation, disrupt operations and harm your bottom line.
The primary goal of good cyber hygiene is risk management. Taking daily, precautionary measures to keep your business’s sensitive data protected against cybercriminals is essential for combating potential threats, including:
In addition to protecting your operations, maintaining proper cyber hygiene is key to staying resilient if an attack occurs.
Improving your business’s security posture with good cyber hygiene practices is incredibly effective for mitigating risks. According to the 2022 Microsoft Defense Report, following basic cyber hygiene practices can prevent 98% of cyberattacks aimed at your business.
Your business can save significant time, money and energy by having your team stick with cybersecurity protocols. Additional benefits include:
Cyber hygiene consists of many smaller practices intended to maintain healthy data environments that align with a few key principles:

The hardware and software solutions your business utilizes for its operations are often major targets for cybercriminals. Addressing vulnerabilities in these systems is essential for combating unwanted threats.
Regularly updating hardware and software can help you keep your systems up to date and equipped to handle newer dangers. Your business needs the latest protections and cybersecurity framework, including firewalls, proxy servers and patches, for the most effective risk mitigation.
Many cyber hygiene practices revolve around securing your hardware and software as best as possible because your business relies on these systems and their data.
Cybersecurity threats continue to grow and wreak havoc on organizations of all sizes. Experts predict the average annual cost of cybercrime will reach $10.5 trillion by 2025, meaning businesses must find ways to improve their cyber hygiene practices. Increasing employee awareness through comprehensive training programs is one effective method for combating cyber dangers and maintaining a secure data environment.
Your team should understand how to identify, address and mitigate common threats. Remind them of the importance of keeping their login credentials private and inform them of the serious risks of a data breach. Help them see their essential role in maintaining cyber hygiene across your entire business.
The final principle of cyber hygiene is effective and comprehensive risk management solutions. The best way to secure your company’s digital network is to continuously look for new weaknesses that could make it easier for a cybercriminal to access your private data. Regular risk assessments will help you find vulnerabilities on your attack surface, allowing you to patch holes before a hacker can capitalize on them.
Explore the following best practices to boost your business’s cyber hygiene:
Working with a cybersecurity professional can help make your business’s cyber hygiene management processes simple.
Every business can benefit from prioritizing cyber hygiene in its overarching information technology (IT) strategy. The following are basic steps for maintaining a secure business environment:
If your business needs comprehensive cybersecurity solutions, turn to the wide range of services from Morefield. With more than 75 years of industry experience, we understand the crucial measures necessary for protecting sensitive data across your digital landscape.
Our extensive cybersecurity solutions are scalable and will help protect the digital processes that are essential to your business’s success. We will guide you through cyber hygiene best practices to ensure your operations are secure.
Are you ready to get started? Contact Morefield to learn more about our IT, cloud and cybersecurity solutions today.
